Difference Between Phishing and Spear Phishing
In spite of the fact that phishing is part technology and part psychology, it is one of the most serious security issues professionals and enterprises face today. Your email systems are more vulnerable to these phishing attacks if unprotected. Such technology is based on a solid understanding of how things may go wrong – whether the vulnerability is on the network, on individual computers, or in the design of user interfaces. Phishing is a form of social engineering in which an attacker tricks people in mass into clicking on malware links to fraudulently retrieve their confidential or sensitive credentials or information. Such communications are more frequently done through emails to target a wide range of people.
Recently, a more target-specific form of phishing called spear phishing has taken on a large role in the security ecosystem. These attacks, unlike, phishing attacks, target specific individuals or groups within organization and use trickery to convince users to click a link, which installs malicious code on their computer. The attacker is then able to collect valuable personal and professional information from the victim and at times, allows them complete control of the victim’s computer. Unlike phishing, it’s a targeted attempt to steal financial information or account credentials from a specific victim. These fraudulent emails appear to come from a trusted source to help attackers steal classified information. Both phishing and spear phishing are the most common forms of email attacks, with a slight difference.
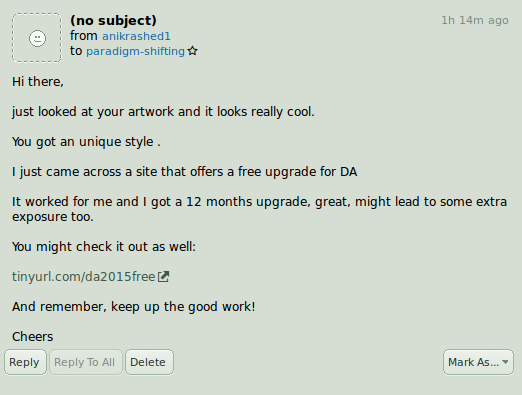
What is Phishing?
Phishing is the most common form of email attack in which the attacker tricks people into clicking into malicious links that appear to be legit, to illegally obtain their sensitive or confidential information by mimicking electronic communications from a trustworthy source or organization in an automated fashion.
There has been an alarming trend of the increase in number of phishing attacks in the past few decades. Phishing is an evolutionary threat in many ways and with the ubiquity of the Internet, phishing becomes a bigger threat for several reasons. First, it can cost the victim real money and second, organizations whose names have been used in a phishing attack, often have to bear the support costs.

What is Spear Phishing?
Spear phishing is the next level of email attack in which the emails are carefully designed to target a specific group or individual and to convince them to click a link, which installs malicious code on their computer. After the malicious code enters their system, the attacker gains full control of their computer and is then able to obtain valuable personal and professional data from the victim.
These attacks are highly dangerous as they are mostly targeted towards high-level corporate employees, most of whom have access to commercial banking, sales databases, and other sensitive information. The attackers often disguise themselves as a reputed organization and the emails appear to be originated from trustworthy sources eventually luring the victims to take the bait.
Difference between Phishing and Spear Phishing
-
Terminology for Phishing and Spear Phishing
– Both the terms phishing and spear phishing can be easily confused because they are the two most common forms of email attacks intended to acquire sensitive and confidential information off the victims disguised as trustworthy entities or organizations.
Both the attacks are carried out through emails or phone calls, social media, or text messages. However, phishing attacks are targeted towards a wide range of people, whereas spear phishing scam is targeted towards a specific individual or group, or at times, organization or business executing a sophisticated targeted attack to gain unauthorized access.
-
Objective
– While both phishing and spear phishing share similar techniques, they differ in objectives. Phishing is more like an exploratory attack that targets a wide range of people, while spear phishing is a more target-specific form of phishing.
In spear phishing, an email is crafted and sent to a specific person within an organization with the sole purpose of infecting his/her system with malware in order to obtain sensitive information. The main objective of spear phishing is to attack large companies or high-value corporate employees which often lead to a much sophisticated and targeted attack.
-
Perpetrator
– The attackers or attacker behind phishing attacks lure their victims to gain valuable or confidential information from them and the information is then used for a number of nefarious deeds such as fraud, identity theft, data stealing, corporate espionage, etc.
There are mainly two groups of attackers who are behind the majority of spear phishing attacks and they share target information and intelligence on the most effective spear phishing attacks. These groups are mostly business-oriented malicious code distributors specialized in social engineering and fraudulent transactions.
Phishing vs. Spear Phishing: Comparison Chart

Summary of Phishing Vs. Spear Phishing
Phishing and Spear Phishing are the two most common forms of email attacks designed specifically for the victims to take the bait, which are mostly in the form of emails, phone calls, and text messages.
While phishing is the most common form of security threat in which an attacker tricks people into clicking on malware links to fraudulently retrieve their confidential or sensitive credentials or information. Such communications are done through emails which are sent in masses. Spear phishing is the more target-specific version of phishing in which the targets, unlike in phishing, are a specific group or individual or high-level corporate employees. Unlike spear phishing, phishing attacks are not personalized to their targets.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: http://www.doncio.navy.mil/FileHandler.ashx?id=6818
[1]Image credit: https://www.deviantart.com/paradigm-shifting/art/deviantART-Account-Phishing-WARNING-550782721
[2]Howard, Rick. Cyber Fraud: Tactics, Techniques and Procedures. Boca Raton, Florida: CRC Press, 2009. Print
[3]Stavroulakis, Peter and Mark Stamp. Handbook of Information and Communication Security. Berlin: Springer, 2010. Print
[4]Jakobsson, Markus and Steven Myers. Phishing and Countermeasures. Hoboken, New Jersey: John Wiley & Sons, 2006. Print
