Difference Between NTLM and Kerberos
The IIS integrated Windows authentication module implements two major authentication protocols: the NTLM and the Kerberos authentication protocol. It calls on three different Security Service Providers (SSPs): the Kerberos, NTLM, and Negotiate. These SSPs and authentication protocols are normally available and used on Windows networks. NTLM implements NTLM authentication and Kerberos implements Kerberos v5 authentication. Negotiate is different because it does not support any authentication protocols. Because Integrated Windows authentication includes several authentication protocols, it needs a negotiation phase before the actual authentication between Web browser and server can take place. During this negotiation phase, the Negotiate SSP determines which authentication protocol to use between the Web browser and the server.
Both the protocols are extremely secure and they are capable of authenticating clients without transmitting passwords over the network in any form, but they are limited. The NTLM authentication does not work across HTTP proxies because it requires a point-to-point connection between the Web browser and server in order to function properly. Kerberos authentication is only available on IE 5.0 browsers and IIS 5.0 Web servers or later. It works only on machines running Windows 2000 or higher and requires some additional ports to be open on firewalls. NTLM is not as secure as Kerberos, so it’s always recommended to use Kerberos as much as possible. Let’s take a good look at the two.
6 1″ src=”https://www.differencebetween.net/wp-content/uploads/2019/05/Difference-Between-NTLM-and-Kerberos.png” alt=”” width=”500″ height=”189″>
What is NTLM?
NT LAN Manager is a challenge-response-based authentication protocol used by Windows computers that are not members of an Active Directory domain. The client initiates the authentication through a challenge/response mechanism based on a three-way handshake between the client and server. The client starts the communication by sending a message to the server specifying its encryption capabilities and containing the user’s account name. The server generates a 64-bit random value called the nonce and responds to the client’s request by returning this nonce which contains information about its own capabilities. This response is called the challenge. The client then uses the challenge string and its password to calculate a response, which it transmits to the server. The server then validates the response it received from the client and compares it with the NTLM response. If the two values are identical, the authentication is successful.
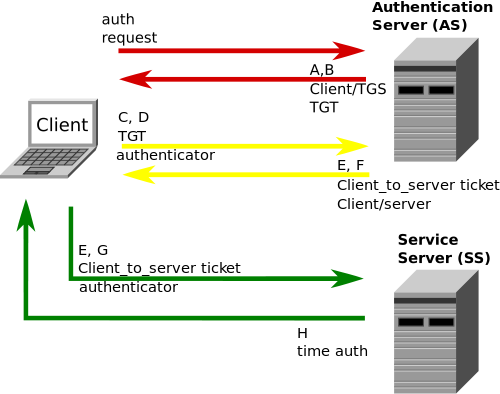
What is Kerberos?
Kerberos is a ticket-based authentication protocol used by Windows computers that are members of an Active Directory domain. Kerberos authentication is the best method for internal IIS installations. Kerberos v5 authentication was designed at MIT and defined in RFC 1510. Windows 2000 and later implements Kerberos when Active Directory is deployed. The best part, it reduces the number of passwords each user has to memorize to use an entire network to one – the Kerberos password. In addition, it incorporates encryption and message integrity to ensure that sensitive authentication data is never sent over the network in the clear. The Kerberos system operates through a set of centralized Key Distribution Centers, or KDCs. Each KDC contains a database of usernames and passwords for both users and Kerberos-enabled services.
Difference between NTLM and Kerberos
Protocol of NTLM and Kerberos
– NTLM is a challenge-response-based authentication protocol used by Windows computers that are not members of an Active Directory domain. The client initiates the authentication through a challenge/response mechanism based on a three-way handshake between the client and server. Kerberos, on the other hand, is a ticket-based authentication protocol which works only on machines running Windows 2000 or higher and running in an Active Directory domain. Both the authentication protocols are based on symmetric key cryptography.
Support
– One of the major differences between the two authentication protocols is that Kerberos supports both impersonation and delegation, while NTLM only supports impersonation. Delegation is basically the same concept as impersonation which involves merely performing actions on behalf of the client’s identity. However, impersonation just works within the scope on one machine, while delegation works across the network as well. This means the authentication ticket of the original client’s identity can be passed onto another server in the network if the originally accessed server has the permission to do so.
Security
– While both the authentication protocols are secure, NTLM is not as secure as Kerberos because it requires a point-to-point connection between the Web browser and server in order to function properly. Kerberos is more secure because it never transmits passwords over the network in the clear. It is unique in its use of tickets that prove a user’s identity to a given server without sending passwords over the network or caching passwords on the local user’s hard disk. Kerberos authentication is the best method for internal IIS installations (websites used only by domain clients).
Authentication
– One of the major advantages of Kerberos over NTLM is that Kerberos offers mutual authentication and aimed at a client-server model meaning the client’s and the server’s authenticity are both verified. However, both the service and client must be running on Windows 2000 or higher, otherwise authentication will fail. Unlike NTLM, which involves only the IIS7 server and the client, Kerberos authentication involves an Active Directory domain controller as well.
NTLM vs. Kerberos: Comparison Chart

Summary of NTLM Vs. Kerberos
While both the protocols are capable of authenticating clients without transmitting passwords over the network in any form, NTLM authenticates clients though a challenge/response mechanism that is based on a three-way handshake between the client and the server. Kerberos, on the other hand, is a ticket-based authentication protocol that is more secure than NTLM and supports mutual authentication, which means the client’s and the server’s authenticity are both verified. In addition, Kerberos supports both impersonation and delegation, while NTLM only supports impersonation. NTLM is not as secure as Kerberos, so it’s always recommended to use Kerberos as much as possible.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/4/4e/Kerberos.svg/500px-Kerberos.svg.png
[1]Image credit: https://commons.wikimedia.org/wiki/File:Metasploit-27-cainsuccesshalflm.png
[2]LeBlanc, David and Michael Howard. Writing Secure Code. London, United Kingdom: Pearson Education, 2002. Print
[3]Macdonald, Matthew and Mario Szpuszta. Pro Asp.Net 2.0 in C# 2005. Hoboken, New Jersey: John Wiley & Sons, 2005. Print
[4]Clercq, Jan De. Windows Server 2003 Security Infrastructures: Core Security Features. Amsterdam, Netherlands: Elsevier, 2004. Print
