Difference Between SHA and MD5
Secure Hash Algorithm (SHA) and Message Digest (MD5) are the standard cryptographic hash functions to provide data security for multimedia authentication. Cryptographic hashes play a fundamental role in modern cryptosystems. So it is important to understand the basic mechanism behind these algorithms and the issues involved in choosing a particular hashing algorithm. Hashing is based on a one-way mathematical function; functions that are easy to compute, but significantly tough to reverse. Hash functions are the basis of the protection mechanism of Hashed Message Authentication Codes (HMAC). It is a major enabling technology for network security used to achieve specific security objectives.
SHA and MD5 are the two well recognized hash functions. The MD5 hashing algorithm takes a message of arbitrary length as input and produces as output a 128-bit “fingerprint” or “message digest” of the input message. It is a one-way function that makes it easy to compute a hash from the given input data. It is a complex sequence of simple binary operations, such as exclusive OR (XORs) and rotations, that are performed on input data and produce a 128-bit digest. The SHA is a potential successor to MD5 and the algorithm specified in the Secure Hash Standard (SHS). SHA-1 is a revision to the SHA standard that was published in 1994. We put together an unbiased comparison between the two hashing functions.

What is SHA?
Developed by the U.S. National Institute of Standards and Technology (NIST), the Secure Hash Algorithm (SHA) is a family of cryptographic hash functions specified in the Secure Hash Standard (SHS). The Federal Information Processing Standard (FIPS 180-2) specifies four secure hash algorithms – SHA-1, SHA-256, SHA-384, and SHA-512 – all of which are iterative, one-way hash functions that can process a message with a maximum length of 264 – to 2128 – bits to produce a 160- to 512-bit condensed representation called a message digest. The input message is processed in 512- to 1024-bit blocks. SHA-1 is a commonly used 160-bit hash function that resembles the MD5 algorithm and is often used by checksum calculators for file integrity verification.
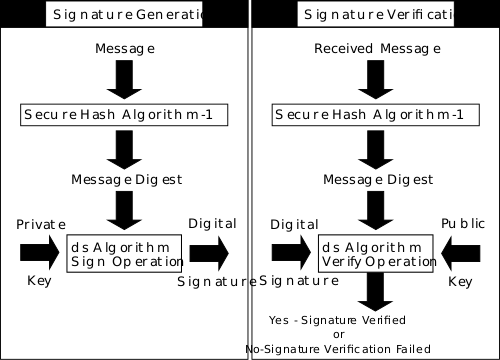
What is MD5?
The Message Digest (MD5) is a ubiquitous hashing algorithm that was developed by Ron Rivest and is used in a variety of Internet applications today. It is a cryptographic hash algorithm that can be used to create a 128-bit string value from an arbitrary length string. Despite of its security vulnerabilities, it is still widely used and deployed, mostly for verifying integrity of files. MD5 is based on its predecessor, the MD4 algorithm. The main algorithm itself is based on a compression function which operates on blocks. The MD5 algorithm takes an input a message of arbitrary length and produces as output a 128-bit “fingerprint” or “message-digest” of the input message. MD5 is not quite as fast as the MD4 algorithm, but offers much better data security. It is commonly used in security protocols and applications such as SSH, SSL, and IPSec.
Difference between SHA and MD5
Basic of SHA and MD5
– The Secure Hash Algorithm (SHA) is a family of cryptographic hash functions developed by the U.S. National Institute of Standards and Technology (NIST). The Message Digest (MD5) is a ubiquitous hashing algorithm that was developed by Ron Rivest and is used in a variety of Internet applications today. It is a cryptographic hash algorithm that can be used to create a 128-bit string value from an arbitrary length string. Like MD5, SHA is also widely used in applications such as SSH, SSL, S-MIME (Secure/Multipurpose Mail Extension), and IPsec.
Message Digest Length for SHA and MD5
– The Federal Information Processing Standard (FIPS 180-2) specifies four secure hash algorithms – SHA-1, SHA-256, SHA-384, and SHA-512 – all of which are iterative, one-way hash functions that can process a message with a maximum length of 264 – to 2128 – bits to produce a 160- to 512-bit condensed representation called a message digest. MD5 algorithm takes an input a message of arbitrary length and produces as output a 128-bit “fingerprint” or “message-digest” of the input message.
Security for SHA and MD5
– MD5 hash is typically expressed as a 32-digit hexadecimal number and is believed to be cryptographically broken and can have collisions. Although, it is one of the well recognized cryptographic hash functions, it is not ideally suitable for security-based services and applications or digital signatures that rely on collision resistance. SHA, on the other hand, is believed to be more secure than MD5. It takes a stream of bits as input and produces a fixed-size output. There are more secure variations of SHA-1 available now, which include SHA-256, SHA-384, and SHA-512, with the numbers reflecting the strength of the message digest.
SHA vs. MD5: Comparison Chart

Summary of SHA vs. MD5
SHA-1 appears to be more secure than MD5 in many regards. While there have been some known attacks reported on SHA-1, they are less serious than the attacks on MD5. There are more secure and better hash functions available now, such as SHA-256, SHA-384, and SHA-512, all of which are practically secure with no prior history of attacks reported on them. Although, MD5 is one of the well recognized cryptographic hash functions, it is not ideally suitable for security-based services and applications because it is cryptographically broken. Thus, MD5 is considered less secure than SHA by many authorities on cryptography. The SHA algorithm is slightly slower than MD5, but the larger message digest length makes it more secure against inversion attacks and brute-force collision.
- Difference Between Caucus and Primary - June 18, 2024
- Difference Between PPO and POS - May 30, 2024
- Difference Between RFID and NFC - May 28, 2024
Search DifferenceBetween.net :
Leave a Response
References :
[0]Furht, Borko. Encyclopedia of Multimedia. Berlin, Germany: Springer, 2008. Print
[1]Liu, Dale. Next Generation SSH2 Implementation: Securing Data in Motion. Amsterdam, Netherlands: Syngress, 2011. Print
[2]Oppliger, Rolf. Security Technologies for the World Wide Web. Norwood, Massachusetts: Artech House, 2003. Print
[3]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/1/16/Fips186-2.svg/500px-Fips186-2.svg.png
[4]Image credit: https://upload.wikimedia.org/wikipedia/commons/thumb/e/e2/SHA-1.svg/576px-SHA-1.svg.png
